Stop tormenting your users with passwords. That’s not nice or secure.
According to a user survey by password management service Lastpass, the average employed person has to manage 191 passwords. This figure could be a bit on the high side, but nevertheless in many services, the Forgot your password? page is the among the most visited pages. That should prove that people need too many passwords. […]
According to a user survey by password management service Lastpass, the average employed person has to manage 191 passwords. This figure could be a bit on the high side, but nevertheless in many services, the Forgot your password? page is the among the most visited pages. That should prove that people need too many passwords.
People tend to be optimistic when it comes to their own cyber security. Many don’t believe that their random accounts are worth hacking into and therefore don’t take passwords very seriously. Last year’s most common password was 123456. Even though 91 percent of people are aware that you should never use the same password for different services, 61 percent do just that. We also share passwords with friends and colleagues even though we know that it’s stupid.
The fact is that the majority of people are too naive, disorganized, careless and/or lazy to manage their passwords appropriately. This causes huge data security risks to both companies and individuals: the weakest link in cyber security is nearly always a somebody instead of a something. Messing about with passwords is also extremely annoying, which adds to the temptation of neglecting password security.
Th1s d0n’t m4K3 s3NS3!
The common habit of mixing big and small caps, numbers and special characters – U_kn0W? – is actually completely pointless. This fiasco can be laid squarely at the feet of a certain Bill Burr.
In 2003, Mr. Burr published the eight-page password guide of the National Institute of Standards and Technology (NIST), which was largely based on a single study carried out in the 80s – in other words, before the internet. Thanks to this completely unscientific guide, we have now been using hard-to-remember but easy-to-crack passwords for decades.
Bill has later admitted that he knew hardly anything about passwords when he was writing the publication. “Much of what I did I now regret”, he says to Gizmodo.
This well-known XKCD strip explains how we could just as well be using a more people-friendly and secure password method if Bill had only done the legwork. But the general public has now become accustomed to thinking up confusing p4S5w0RdS, many services still require them, and the habit is not easy to kick.
Sending out an SOS won’t save you from passwords, but another SSO might help
Single sign-on or SSO means opening the door to several services managed by the same provider with a single login. Even a normal password can be used as an SSO solution but other, more humane methods are possible.
Qvik has an example that illustrates the point perfectly. We renewed the login process for Tallink’s services by enabling users to sign in with their e-mail address, telephone number, Google account or the good old username-password combo.
“Users can proceed in the login process as long as they can provide some piece of information about themselves”, says Qvik’s Head of Design, Matias Pietilä. “Before, many users logged in through the Forgot your password? page. Now they can just ask the service to send them a login link via e-mail or a code by SMS.”
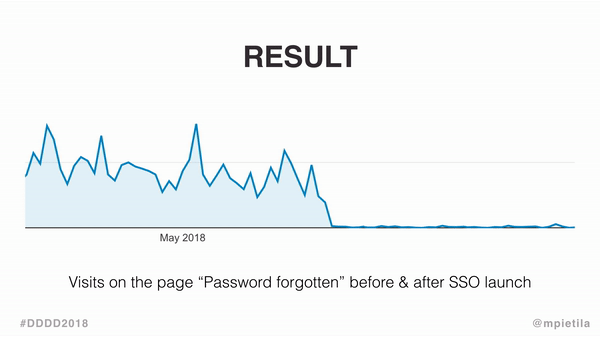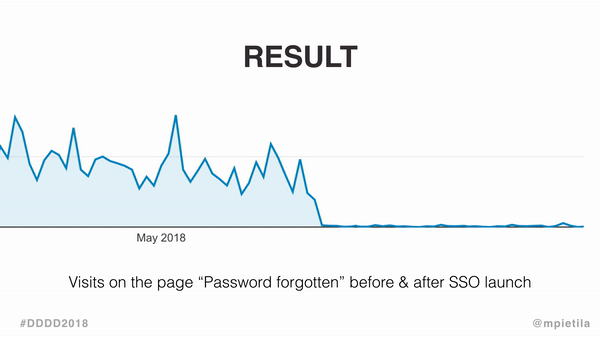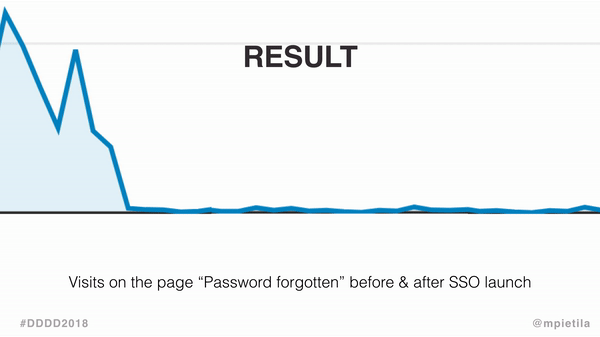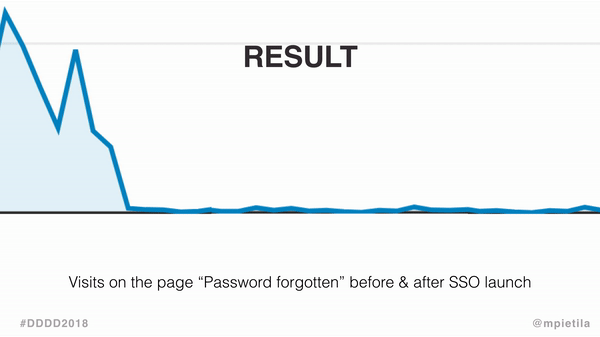
The change caused Forgot your password? page visits to plummet, and the following graph gives you some idea of how much.

See the difference? Maybe the zoom will help.
“Authentication is crucial, because it affects both customer acquisition and retention”, Pietilä says. “Even though this area is business-critical, it’s also often the one that gets the short end of the stick.”
Tallink-style SSO is particularly suitable for services that you don’t log into very often or in which you stay logged for long periods of time. Waiting for a login link or code might not be so much fun after the second or third time in a day. But you can avoid making the user log back in all the time by extending the duration of sessions.
A more secure alternative to normal passwords
Authentication is usually based on three common elements or their combinations. To log in, users either need something only they know (like a password), something they own (i.e. a phone or card with a chip) or something that’s a part of them (a fingerprint or another biometric identifier). Weak authentication only asks for one of the above, while strong authentication requires at least two.
Authentication terminology also includes the separate concept of two-factor authentication, which requires both something that users know (e.g. a username) and something only they have access to, such as a phone or e-mail account.
“A two-factor SSO solution like the one implemented for Tallink is not foolproof, but still more secure than a normal password”, says Pietilä. “It is not a strong authentication method, however, which rules it out for applications such as financial services.”
The weakest link in Tallink’s model is the e-mail, although text messages have some security concerns of their own. If additional security is required, you can use push notifications and add biometrics to the authentication chain.
The brute force attacks commonly used to hack passwords are nevertheless powerless against Tallink’s SSO solution, unless the attacker has access to the target’s phone or e-mail. These types of single sign-on solutions also improve general data security, because sloppy users don’t have to expose their weak or shared passwords to hacking in so many services.
Doesn’t it sound lovely?
By now, you should be convinced that all services that require authentication should offer other solutions in addition to passwords. And we mean now. But if you would still like to torment your users with passwords, here are some additional tips from Head of Design Pietilä to make logging in true hell.
1. Force users to make up unique usernames
Having to remember service-specific usernames in addition to passwords will annoy your users even more. The greatest frustration is achieved by trying out different username-password combinations and trying to remember which went with what.
2. When users reset their passwords, automatically assign a new password made up of gibberish and numbers
Don’t give your users the option of creating a new password directly. E-mail them an un-rememberable string of characters and digits and have them find the Change your password section themselves. This will be sure to elicit at least a sigh of frustration.
3. Don’t accept special characters
Thanks to B!LL Bu#r1, users have gotten into the habit of choosing passwords rife with special characters. Even though they have no impact on data security, users will think it’s stupid that their difficult passwords are suddenly no good. This can mess up the user’s password logic.
4. When users enter the wrong password, also erase the username for the next try
When it comes to your spare time, nothing compares to typing and retyping your password. Nothing, that is, except also getting to enter your long username again and again. This will be sure to catch your users’ attention on mobile devices in particular.
5. Do your level best to forget any information whatsoever entered by your users
Make your users re-enter all of their details every time, even if your service already contains the information. We’re talking addresses and personal data here. When your users get used to other services that complete all possible fields automatically, they will hate the pointless typing, and eventually your service, even more.
Illustration: Aija Malmioja

